His articles have appeared in many respected technology publications. Ruheni explains complicated technical concepts clearly and simply. However, most are outdated and have not kept up with the changing landscape. For example, DuckDuckGo is the most popular but often shows repetitive results and is sometimes unrelated to the question. The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China.
Dark Web Child Abuse: Hundreds Arrested Across 38 Countries

There is a range of (legal) dark web browsers and deep web search engines. Another point is it does highlight that, even though the list is enormous, hidden services are discoverable. I will at least leave Onion search engines are still running as of February 17, 2025.
Other Dark Web Sites Offering Email Services
ProPublica joined the Dark Web to protect themselves and keep their journalists safe. On the one hand, this is considered beneficial for people living under strict regimes where censorship is common. On the other hand, it can lead to trolling, the spread of misinformation, and unsavory comments that users wouldn’t be allowed to make on the surface web. Reddit is actually available on the dark web now, so there’s no need to rely on third-party tools to access it via Tor. Just bear in mind that the addition of anonymity to a platform like Reddit causes people to behave without a filter.
It provides a safe haven for anyone looking to shed light on wrongdoing or share critical information with the media. ZeroBin is an attractive option for anyone looking to share sensitive information without compromising privacy. It’s particularly useful for journalists, whistleblowers, and those who urgently need to send or receive confidential data.
ZeroBin — The Secure Way To Share Your Pastes
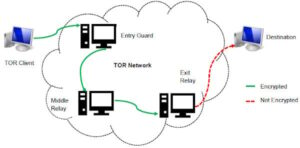
Each server adds a layer of encryption, and this layered system is what lends The Onion Router its name. Watch for unexpected changes in system performance that could indicate malware. Cryptocurrency miners and other malicious software often target dark web users. Using a reliable antivirus to scan your device is worthwhile if you spot suspicious spikes in system resource usage. This isolates any potential malware and prevents cross-contamination with your personal data.
Should I Use A VPN To Access Tor?

Its clean interface and lack of ads make it much easier to use than other dark web search engines. However, many are used for illegal activity and onion websites are often popular hangouts for cybercriminals and scammers. Using common sense like avoiding clicking on shady links or download buttons, sticking to known sites and adding a VPN for an extra layer of protection, you should be fine.
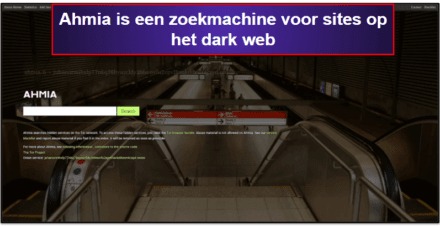
For instance, if you use it to search for social media sites like Facebook, it will not show you the onion link for the website. It will show you posts on Facebook-related topics, such as where to buy stolen Facebook accounts, how to hack Facebook accounts, etc. That said, Ahmia can help you find working onion links, which you can then use via the Tor browser. Ahmia will automatically remove content that contains child abuse but will not do so for other types of content, such as adult content so you have to adopt a cautious approach. Tor project coined the term Onion Routing (TOR stands for The Onion Router) to describe the process by which users gain online privacy and anonymity using the network. Tor works by directing internet traffic through a global network of volunteer nodes.
- It’s a part of the internet that’s less regulated and more shadowy, for better and for worse.
- Protect your business with end-to-end encryption and compliance-ready security.
- A VPN provides strong security for everyday browsing without the extra delays, middle checkpoint, and then finally the exit gate.
- Many news publications, like the ones listed above, have a SecureDrop on their .onion sites.
Top 10 Best Dark Web Search Engines In 2025 Safe &
It attracts RaaS affiliates and credential sellers, leveraging a partners program to expand its reach. With nearly 50,000 members, its community thrives on open discussion. Notably, LeakBase bans data leaks involving Russian entities, indicating a politically calculated stance seen in many dark web forums.
Onion Links Directory 2025
You can find legitimate and active onion addresses using Dark.Fail, which is run by an anonymous journalist. You can rest assured that the links you find on Dark.Fail will not be dubious ones, so the chances of getting scammed are pretty low here. Torch is the oldest and largest .onion search engine with more than 1 million .onion sites indexed. Just bear in mind that many of those will be out of date, and using this index will require a lot of discretion, due to its size.

Former ICE special agent Richard Nikolai Gratkowski and border patrol agent Paul Casey Whipple, both of Texas, were arrested on child porn charges in connection to Welcome to Video. Gratkowski, 40, who pleaded guilty to intent to access child porn, was sentenced to 70 months in prison and ordered to pay $35,000 in restitution to seven victims. Whipple was also charged with production and distribution of child porn. Remember to access the Deep web links in a safe and anonymous way.
Vorm Web focuses on quality over quantity and splits findable results into three security categories, from secure to risky. While it doesn’t index dark web content, it’s the default search engine on the Tor Browser because of its strong privacy features and lack of tracking. For searching within the dark web, specialized tools like Torch are better, as they specifically index .onion sites and hidden content. It’s simply a part of the internet that isn’t indexed by regular search engines and needs special software, like Tor, to access. However, while browsing the dark web itself is lawful, taking part in illegal activities — like buying or selling illegal goods or engaging in criminal behavior — is not.
Users gained access to videos using tokens bought using cryptocurrency or earned through tasks, such as categorising videos or uploading abusive material. On average, 3.5 new videos were uploaded every hour, many of which had never been seen by investigators before. Some of those arrested not only uploaded and watched videos – but also abused children themselves.

If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites. George is a seasoned Cybersecurity writer who has been writing guides and news about digital security for over five years. He has worked for several international tech platforms, and his writing and editing expertise has also enhanced over time. He loves covering topics about VPNs, online privacy, and anonymity and shares his knowledge of online security with internet users through his words.
Cybercriminals are out there, ready to exploit unsuspecting users, raking in massive sums by hacking devices and blackmailing their victims. It isn’t illegal to simply visit a website on the dark web, but many sites engage in illegal activity. If you participate in illegal activity in any way, you’re breaking the law. It’s a great way to start exploring what the dark web has to offer, but be aware that its links may lead you to scam websites, websites offering highly illegal content… or worse. To access an onion website, simply open its onion link in the Tor Browser or, if using one of Proton VPN’s Tor special servers, inside your regular browser.
But finding reputable onion links and dark web websites can be a challenge. That’s why we took the guessing work out of it for you, and made this list of the best dark web sites you should check out. To protect your data from the websites you visit, one of the most effective steps is to hide your IP address, which can reveal your location, identity, and browsing habits. Using a virtual private network (VPN) masks your real IP by routing your internet traffic through a secure server, making it appear as though you’re browsing from a different location. A VPN also encrypts your connection, keeping your data safe from surveillance and unauthorized access. While they make accessing Tor-hidden websites easier without the Tor browser, they can compromise your privacy and security by acting as intermediaries that might expose your data.