Always exercise caution, be mindful of the content you access, and trust your instincts if something feels off. These resources are just a few examples of the tools available for anonymous communication on the Dark Web. They offer users various options to protect their identities and communicate securely. However, it is important to remember that despite these tools, complete anonymity on the internet is challenging to achieve.
The 12 Best Deep Search Engines
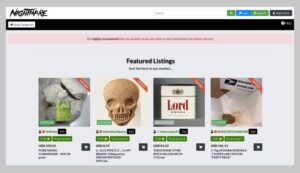
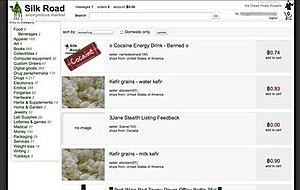
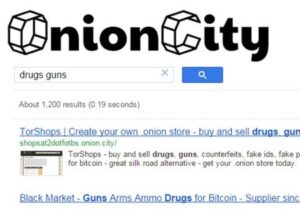
This can include the sale of drugs, weapons, stolen data, and counterfeit items. A dark web search engine allows you to access sites that aren’t listed on traditional search engines like Google and Bing. These websites live on the unindexed, hidden part of the internet known as the dark web. And many people use a VPN with Tor, because while the Tor network offers anonymity and privacy, extra security is recommended when accessing the dark web. While the surface web is easily accessible, the Dark Web offers anonymity, uncensored content, and resources that are hidden from traditional search engines like Google or Bing. But accessing this hidden part of the internet safely requires reliable Dark Web search engines — tools that help you explore the darknet without compromising your identity or security.
How To Set Up And Use The Tor Browser To Search onion Websites

Individual profile viewing options for vendors & marketplaces are also available including details like ratings, mirror links, number of listings, and uptime percentage. You can visit Recon by following its .Onion link here and just in case you manage to bypass its DDoS protection captcha page let us know in the comment section because we failed to do so. Yippy is a search engine that started in 2009, since then it has evolved. To become a leading provider of business learning and knowledge for all types of data users and consumers. This virtual bookstore is one of the oldest search engines on the internet.
Dark Web Reveals Tech Companies Leak Most User Data

Businesses can scan for leaked data or cyber threats using premium engines like Haystak for monitoring forums and marketplaces. Integrate with tools like dark web monitoring services for alerts on credentials or IP theft. Tor updates, like V3 to V4 onion transitions, improve security but may deprecate older .onion addresses, forcing engines like Haystak to reindex and update support. This enhances privacy against attacks but causes temporary downtime or broken links. Consequences might include ISP monitoring, data breaches, or penalties if your actions violate local laws, such as in regions with strict internet censorship. Always use a VPN, verify links, and stick to legitimate purposes to minimize risks.
Avoid Sharing Personal Information
If you’re in London and need assistance with downloading or setting up the Tor Browser, you can also reach out to various IT companies in London that offer expert support services. The Tor Browser, as we know it, is available for Windows, macOS, Linux, and Android. To download the Tor Browser, visit the official website at Torproject.org. Once you’re on the website, click “Download Tor Browser.” Then, select the appropriate version for your operating system and follow the prompts to complete the installation. Not Evil is a reflection of what the community is looking for and what the community reports as abusive or inappropriate content. One notable feature is its “I’m feeling lucky” button, reminiscent of Google’s counterpart, which displays searches for a random keyword chosen from popular searches on OnionLand.
Hidden Wiki
In addition, Ahmia and Haystack make every effort to filter out and blacklist sites known to contain harmful, abusive, or illegal content. This makes them a safer (though still not foolproof) option for searching the Dark Web. The nice thing about Ahmia is that it lists .onion sites that want to be found.

Myth 6: More Than 90 – 96% Of The Internet Is Made Up Of The Dark Web
It routes users’ traffic through thousands of volunteer-run servers called nodes/relays. These nodes/relays and the websites operating on them make up the Tor network, or as it is more generally named, the dark web. Offering more than 100 terabytes of data or over 700 billion web pages, it gives you the history of any public site. It’s worth mentioning that the content found on the Dark Web can vary widely, ranging from legitimate websites focused on privacy and anonymity to illicit marketplaces and forums. To conduct effective searches, it is essential to have a clear understanding of what you are looking for and navigate the Dark Web with caution. It’s crucial to approach the Dark Web with caution and a firm understanding of its risks.
Words Of Caution When Using Dark Web Sites
It’s recommended not to be too vigilant here and leave the investigation to the professionals. Some services are genuine; you can get what you want at an agreed fee. It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals. Be sure that your experience with Whonix will be comparable to Tor because both programs share the same source code.
- You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here.
- Tools like Flare empower your team to conduct reconnaissance on the dark web, scanning for stolen data and other information that might jeopardize your systems and networks.
- If there has ever been a time when you wanted to look at a backlog of the world’s historical newspapers, Elephind is for you.
- Dark web search engines are the gatekeepers to the Tor network’s hidden corners, empowering users to explore what’s intentionally unindexed.
- A network browser gives you access to sites with the ‘.onion’ registry operator.
While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. Make sure that when you download the Tor file, it’s from their official website. It’s impossible to access the dark web with a regular browser like Chrome or Safari. As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously.
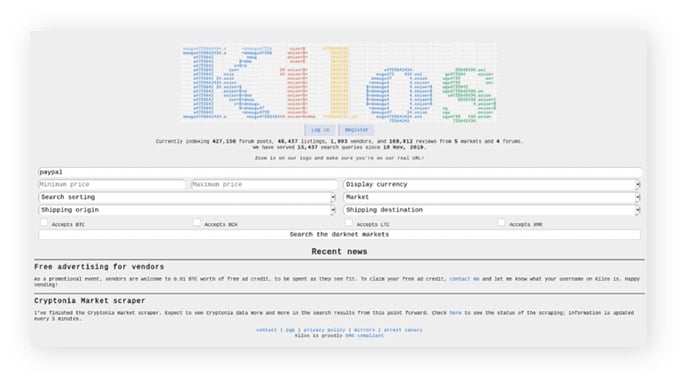
While not Evil does not claim divine authority, it relies on user feedback to identify and address problematic links or hosts. DuckDuckGo doesn’t log your activity, so your search habits, dark web or not, remain private to you. The only downside to DuckDuckGo is that it might show you fewer dark web search results compared with the other search engines on this list. One thing to be wary about is that, like most dark web search engines, Torch doesn’t filter websites. This increases the likelihood of stumbling onto a malicious webpage or harmful material. Kilos is a dark web marketplace search engine that lets users search for specific products they’re looking for.
Report via the engine’s community mechanisms, like Ahmia’s GitHub for blacklisting or NotEvil’s volunteer reports, or submit to Tor Project forums anonymously. They operate on Tor, encrypting queries end-to-end, but users must still enable “Safest” mode and use VPNs to prevent leaks. This makes them superior for privacy advocates, though opaque operations in some (e.g., Torch) can raise concerns.
When it comes to the best dark web search engines, there are a few things to keep in mind. First and foremost, you want a search engine that is private and secure, as well as one that can be used anonymously. The Tor network consists of a series of volunteer-run servers that route internet traffic through a series of encrypted tunnels. This makes it difficult for anyone to track your online activity or identify your location.
Many need to cross international borders, and customs officials are cracking down on suspicious packages. The dark web news site Deep.Dot.Web teems with stories of buyers who have been arrested or jailed for attempted purchases. Dark web forums are online communities where individuals participate in discussions on a wide range of subjects, from technology and privacy to more illicit matters.