
The Dark Web Monitor (DWM) employs a snowballing approach, a widely used web crawling technique, to collect and organise data from the dark web. This process starts with a curated list of seed addresses sourced from platforms like Ahmia.fi. The crawler iteratively retrieves and parses webpages using these initial seeds, extracting new URLs to expand its network coverage.
Common User Mistakes To Avoid

Anyone can access the deep web by using specialized search engines, dedicated web directories, and other sources that can help you find the data or information. The invisible web is made up of data and information that is not indexed and cannot be searched for by using traditional search engines. Content includes non-indexed websites, apps, and resources, which can include protected information such as, online banking, specialized databases, non-linked and password-protected websites, and more. It includes media and archives which cannot be crawled and indexed with current search engine technology.
Law Enforcement Efforts To Combat Cryptocurrency Use On The Dark Web
Other than the Silk Road 2.0, similar marketplaces also emerged, but they all went down sooner or later. Another dark net marketplace that has grabbed a lot of attention is the Hydra market. The entire website is in Russian, but the vendors are present worldwide. It accepts payments through Bitcoin and the Escrow system and ensures that your identity remains anonymous during your purchases. The White House market offers impressive features like a mandatory PGP requirement that enables 2FA for the user’s profile and adds a protective layer. The browser uses onion routing technology to route the internet traffic through multiple relay nodes that provide layered encryption.
- Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data.
- You can find items like digital goods, software, and even collectibles.
- This article explores how individuals can safely acquire cryptocurrency anonymously, minimize potential exposure, and maintain their privacy and security online.
- While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store.
- The advantages of I2P are based on a much faster and more reliable network.
Buying Bitcoin Anonymously (More Or Less)
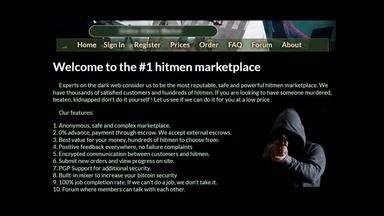
Eventually, the system collapses, and most people lose their entire investment. It’s also a marketplace for digital mercenaries; you’ll find everything from solo hackers offering their skills to well-organized groups that take on more complex or high-stakes projects. Some even have connections to criminal organizations and, in more serious cases, government-backed operations. In many countries, strict laws limit who can legally buy, own, or carry firearms. So when someone like a private buyer or criminal group can’t pass the background checks or get the right permits, they usually turn to the dark web to sidestep the rules and get armed without drawing attention.
This is an excellent way for Dark Web users to provide additional privacy protection when accessing the Dark Web. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online. Silk Road became one of the most famous online black markets on the dark web for illegally selling drugs. Pixel Privacy believes in digital privacy and does not believe in using it for heinous and/or illegal activities, and so the focus of this article will be on legal activities.
Noones: Peer-to-Peer Platform For Larger Trades
Data for the study was gathered from the Dark Web Monitor and Iknaio Cryptoasset Analytics. A four-step process was used to identify BG sites and their Bitcoin addresses from 2 million dark websites. BidenCash is considered to be one of the most popular credit card sites today and serves as the official sponsor of the popular credit card site Crdpo. Are you worried that your Bitcoin transactions are secretly being tracked? Bitcoin transactions are pseudonymous which means that if someone ties a bunch of numbers to your identity your whole financial transaction history could be exposed.

Report It To The Authorities (if It’s Safe To Do So)
You can meet in person, pay with cash, and receive your Bitcoin with no ID required for small amounts. Be sure to check the reputation of any seller before trading to avoid fraud. By sending your coins through multiple wallets before the final recipient, you create a confusing trail that is hard to follow. When you purchase Bitcoin on a centralized exchange, you expose your data to leaks and hacks and may be at risk. Not only is your online identity at risk, but your physical self is also challenged.
A Guide To Anonymous Bitcoin
- These platforms continuously scour the deep and dark web, looking for any traces of your sensitive information.
- After a major external shock in 2017, the S2S network shrinks but, unlike the multiseller network, recovers, and grows again (though slower than the multibuyer network).
- Websites support the rhetoric of neo-Nazis, whitesupremacists, and other extremist groups.
- We’ll cover their features, fee structures, and how you can buy Bitcoin without ID verification.
- A Bitcoin mining pool is a collective gathering of excavators who join their registering capacity to tackle complex numerical issues quicker.
- These days, it lists over 11,600 illegal items, including hard drugs, hacking tools, and all kinds of cybercrime services.
These activities take advantage of the decentralized nature of the blockchain technology that powers cryptocurrencies, making it difficult to trace and recover stolen funds. Overall, dark web Bitcoin transactions have a significant impact on price volatility. The anonymity and privacy provided by the dark web make it an attractive platform for conducting illegal activities using Bitcoin. As long as the dark web exists, it will continue to affect the price stability of this popular cryptocurrency.
Bitcoin is pseudonymous, not anonymous, meaning your transactions can be traced back to you with some work. If you want to stay under the radar and buy Bitcoin anonymously, you’ve come to the right place. This guide will show you the best ways to hide your identity when buying crypto. Whether you want to invest in Bitcoin without raising red flags or make untraceable transactions, these methods will help you fly under the radar. Staying anonymous does take some work, but with a few extra steps, you can ensure that your Bitcoin buys stay private and no one will be the wiser.
Searching For Revenue Of Dark Web BG Sites
Such markets are typically accessible through the Tor network, which anonymizes traffic by routing it through multiple relays and encrypting each layer. This encryption makes attribution and tracking more difficult for authorities and cybersecurity professionals. The future of cryptocurrencies and the dark web is uncertain, as both continue to evolve and adapt to new challenges.

The Beginner’s Guide To Buying Goods On The Darknet

Governments can impose regulations that require cryptocurrency exchanges and wallet providers to abide by know-your-customer (KYC) and anti-money laundering (AML) regulations. These regulations aim to make it more challenging for criminals to use Bitcoin on the dark web while preserving privacy and decentralization. However, the use of Bitcoin on the dark web has raised concerns among law enforcement agencies and governments worldwide. While the technology behind Bitcoin provides privacy and anonymity, it also makes it challenging to trace transactions and hold individuals accountable for their activities on the dark web.
Updated Search Terms From Badawi Et Al
The dark web, a hidden part of the internet that can only be accessed with special software, has become the perfect platform for these illicit activities. Overall, dark web bitcoin exchanges and wallets provide a means for individuals to engage in anonymous transactions using the cryptocurrency. However, it is essential to understand the risks involved and take necessary precautions to protect oneself from scams and fraudulent activities. On the surface web, transactions and activities are more traceable and regulated. Users often share personal information, use credit cards or other traditional payment methods, and submit to terms of service and privacy policies. The surface web is governed by laws and regulations that aim to protect individuals and maintain a level of accountability.



