Just like Google, the dark web has some search engines present on it. Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results. You can choose the best darknet (.onion) website that suits you and start surfing. For safer browsing, it is highly recommended to also use a VPN and antivirus software. That said, many of the actors on the dark web are highly skilled digital adversaries who can easily outmaneuver basic security measures. As a leading cybersecurity vendor, CrowdStrike cautions all organizations and individuals to refrain from using the dark web.
Examples Of High-risk Activities:
Along with this, many dark web sites use decentralised hosting, which means they aren’t stored on a single server that can be easily shut down or traced. Analytics Insight is an award-winning tech news publication that delivers in-depth insights into the major technology trends that impact the markets. The content produced on this website is for educational purposes only and does not constitute investment advice or recommendation.
How To Get Your Information Removed From The Dark Web
It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites. It offers top-of-the-line security and fast speeds for a smooth browsing experience on the dark web.
Ways To Improve Cybersecurity Function While Spending Less
Users navigating this space should exercise caution and be aware of the potential legal consequences tied to specific content and transactions. While the initial intent of Tor was to safeguard communication for military and government personnel, it quickly gained traction among privacy advocates and individuals seeking to evade censorship. Consequently, the Dark Web as we recognize it today started to take shape, with websites and services specifically designed to operate within this hidden network. The history of the Dark Web is intricately tied to the development of internet technology and the ongoing pursuit of online anonymity. The concept of an encrypted, hidden layer of the internet began taking shape in the 1990s.
- If you use Tor to access the dark web or unblock websites, connect with a VPN for extra security.
- Even when explaining what is Dark Web, one should not focus only on negative cases.
- The difficulty is maintaining a dark web social media network presence that remains anonymous.
- One of the most insidious dangers on the dark web is not just technical malware or hidden exploits, but the human element—scammers and con artists who rely on psychological manipulation.
In the U.S., dark web usage has been growing steadily—not just among cybercriminals, but also among privacy-conscious users. Cryptocurrency activities, discussions and communities, and even academic resources further populate this hidden corner of the internet. However, it is crucial to recognize the dual nature of the Dark Web, understanding that while it has legitimate uses, it also harbors risks and associations with unlawful activities.
The dark web offers a marketplace section where users can buy legal or illegal products. These products are often bought with cryptocurrencies, and several markets thrive from this exchange to sell or buy products and services. Some popular marketplaces include AlphaBay (before it was taken down) and Hansa.
Dark Web Price Index
Tor can be used together with a VPN to provide overlapping layers of privacy and anonymity. Unlike typical web browsers, Tor Browser uses onion routing, which encrypts and routes traffic through multiple servers around the world to hide your IP address and provide private browsing. In addition, all domains on the Tor network end with the top-level domain .onion (instead of .com). The many layers of an onion represent the multiple layers of encryption in the Tor network.
How Do Individuals Get On The Dark Web?
Accessing this hidden part of the internet requires specialized software such as the TOR Browser and a Virtual Private Network (VPN) to maintain security and anonymity. However, the dark web is also known for being a hub for illicit activity. Anonymous marketplaces (such as The Silk Road) offer everything from recreational drugs and forged documents to firearms and malware toolkits. While accessing the dark web itself is not illegal in most countries, engaging with illicit activities or even visiting suspicious websites can attract the attention of law enforcement agencies. On the legitimate side, the dark web provides a platform for whistleblowers, journalists, and activists operating under oppressive regimes. For instance, platforms like SecureDrop allow individuals to anonymously share sensitive information with news organizations, bypassing censorship and surveillance.
Staying On Top Of The Hacker Underground
In 2023, however, it was estimated that the dark web had more than 2.5 million daily visitors. While the dark web is often portrayed as a haven for illegal activity, this is only part of the story. There are legitimate uses for the dark web as well, particularly for those seeking privacy in countries ruled by oppressive regimes or for individuals who want to maintain anonymity online.
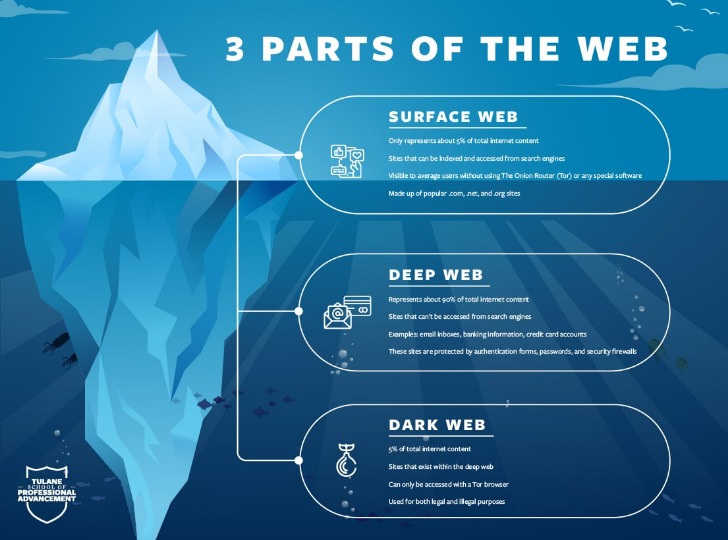
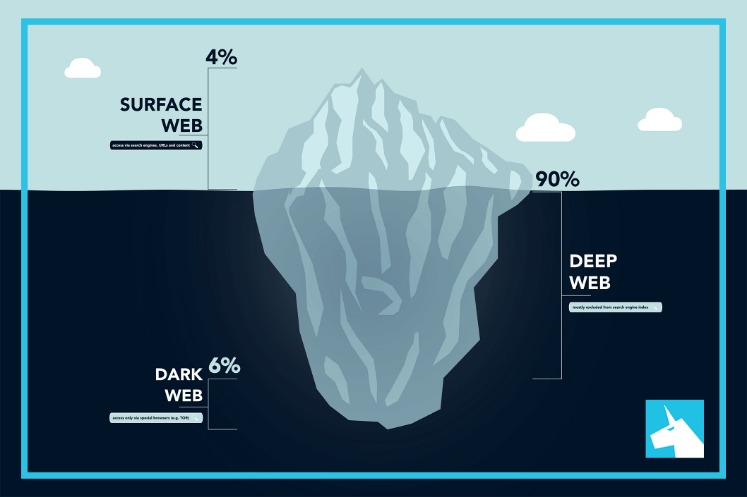
So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. Make sure that when you download the Tor file, it’s from their official website. It’s impossible to access the dark web with a regular browser like Chrome or Safari. As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously.
- In addition, all domains on the Tor network end with the top-level domain .onion (instead of .com).
- These networks are made of small Peer-to-peer (P2P) networks as well as larger networks like TOR.
- Using the Tor browser is simple, but knowing when to fire it up is more complicated.
- The sharing of illegal pornography and discussion of illegal sex acts account for a significant portion of dark web traffic.
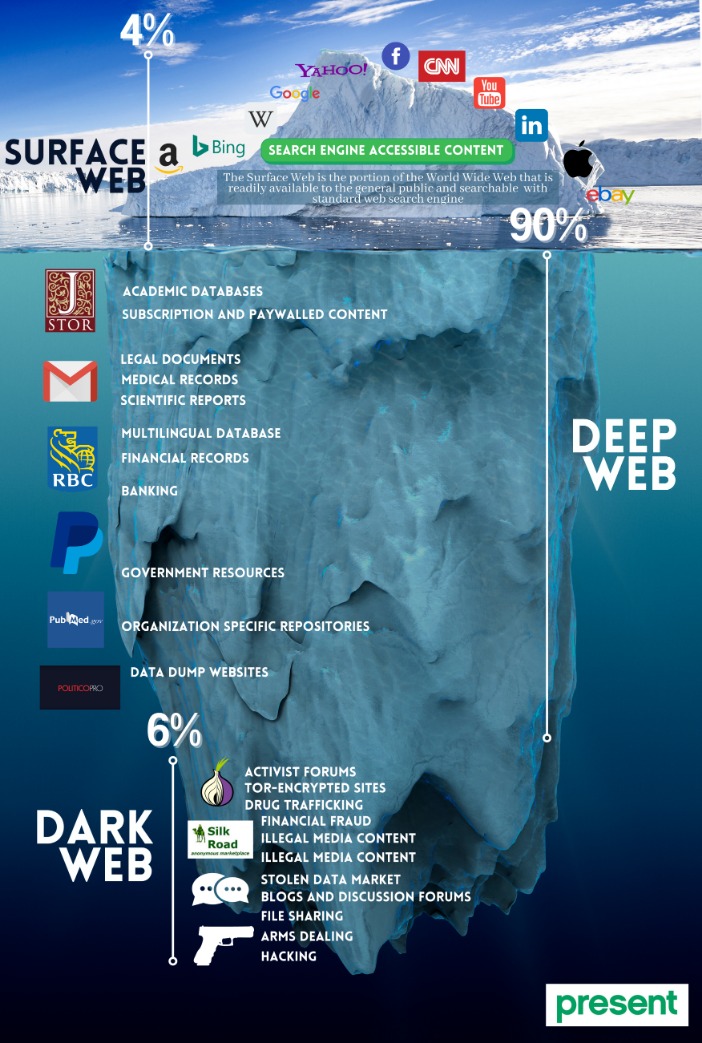
- From databases to intranets to websites waiting to be launched, Deep Web content is usually hidden behind a username and password or other security measures to keep it safe.
But of course, these benefits can be easily extended to those that want to act outside of the constraints of laws in other explicitly illegal ways. That said, a significant chunk of U.S.-based activity on the dark web still revolves around illegal marketplaces—selling things like stolen data, counterfeit documents, and even drugs. Staying cautious is essential when interacting with content on the dark web, as illegal activities are prevalent. Users should refrain from clicking on unverified links and exercise discretion in revealing personal information. Tor, designed by mathematician and computer scientist Roger Dingledine, along with two colleagues, emerged as an open-source project in the early 2000s.

However, Bitcoin’s relevance in the digital world has also made it a scam target. Law enforcement agencies frequently target sites that distribute child pornography. For Example, In May 2021, authorities in Germany brought down Boystown, a child pornography network with more than 400,000 registered users. Several pedophile chat sites were also dismantled, and four people were detained, one of them a Paraguayan suspected of running the network. Terrorist groups have used the dark web since its inception due to its anonymity and lack of regulation. The dark web provides these groups with chat platforms to inspire terrorist attacks and ‘How-to’ guides to teach people how to become terrorists and hide their identities.
It’s a segment of the internet hidden from view, not showing up in search results or accessible through regular web browsers. To enter this hidden world, users rely on the Tor browser, a specialized tool designed to keep web activity private by bouncing it through a network of relays around the globe. This part of the internet also uses advanced encryption, which helps both those visiting and hosting sites to stay anonymous. And finally, there is the Dark Web which is not just a place for criminal activity!
Before visiting any dark websites, get comprehensive cybersecurity software to help protect yourself from threats you may encounter. Dark web browsing is not as simple as regular web surfing, but there are some tools you can use to chart your journey. Dark web search engines and forums like Reddit can help you find reliable dark websites, and you’ll need to use a dark web browser to visit them. The dark web refers to content on the internet that is intentionally hidden and requires special software like Tor Browser to access. The dark web is a subset of the deep web, which is all content on the internet that isn’t indexed by search engines.
Dark web websites won’t show up on Google, but they are indexed by dark web search engines such as Torch. The biggest and most frustrating part about dark websites is that they live for a short span of time. These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites.



