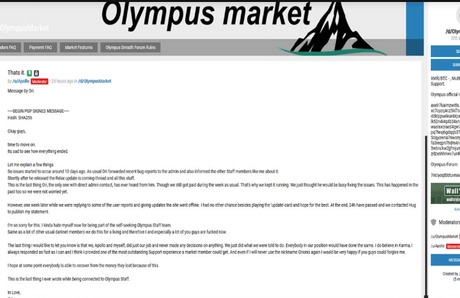
Dark web websites are hidden under layers of encryption that cloak user activity, which can be a boon to whistleblowers, activists, and others who don’t want anyone tracking their activity. Kerberos has grown rapidly — some reports note over 1,100 listings within seven months, while others claim 5,000+ listings — showing a strong vendor presence. User feedback on darknet forums is mostly positive, citing reliability and smooth transactions, though, as with all darknet markets, risks remain. The marketplace has an intuitive interface and offers powerful search tools that make it easy for you to find products from both local and international sellers. All vendors are vetted before they are allowed to sell, so it makes sure of trust and quality.
It allows you to search for images, maps, files, videos, social media posts, and more. It may initially look abandoned, but the community members will answer your questions. It aims to advance research on terminal illnesses like cancer with access to unbiased scientific publications. Sci-Hub is a massive database that eliminates the barriers to getting scientific knowledge. It contains millions of scientific research documents from around the world.
Which Darknet Markets Are Still Open
Despite its name, the marketplace operates primarily in English and serves a global audience. It has gained a reputation for being a reliable source of high-quality data for cybercriminals. It is one of the most notorious credit card shops on the dark web. It has built a reputation for being a reliable source of stolen credit card data and PII.

Vorm Web Search Engine
- Saheed Aremu passionately advocates for digital privacy and cybersecurity in the modern digital age.
- Farwa is an experienced InfoSec writer and cybersecurity journalist skilled in writing articles related to cybersecurity, AI, DevOps, Big Data, Cloud security, VPNs, IAM, and Cloud Computing.
- This traditional search engine is also compatible with the dark web and can help you find dark web websites.
- There’s no guarantee that placing an order with any DNM vendor will be safe or shipped.
- It’s only possible to access onion sites through the Tor browser or by setting up some special network configurations.
- There is no need to visit darknet marketplaces yourself to know whether your data was leaked.
AVG Secure VPN masks your IP address from other internet users, the websites you visit, and even government surveillance. And thanks to ultra-secure, end-to-end encryption, your online activity is obscured. By exploring these categories of resources, users can discover that the dark web’s landscape is more nuanced than popular portrayals suggest. Education, activism, journalism, and creativity all find refuge here, protected by layers of anonymity.
Impact Of Law Enforcement And Policy Changes
- However, make sure you’re careful which links you click on — some of them lead to sites that contain illegal content and services.
- In a way, it feels more like a private club than an open market, and that’s exactly how the operators want it.
- It offers a wide range of products, including drugs, counterfeit money, and stolen data.
- This guide provides verified .onion links, market stats, and expert insights into Tor and Monero usage as of February 21, 2025.
- Below, I’m breaking down each market with everything I’ve picked up—listings, quirks, the works.
Established in 2012, the platform is a time capsule that collects snapshots of websites. These onion addresses will remain online even if the original page disappears. It also keeps the graphical copy and text of the page for better accuracy. Hence, if you participate in them, whether knowingly or unknowingly, you can end up putting criminal charges on yourself, and in some extreme cases, even imprisonment. If you know the right websites, you can easily access a tremendous amount of information, including research articles, news stories, and more.
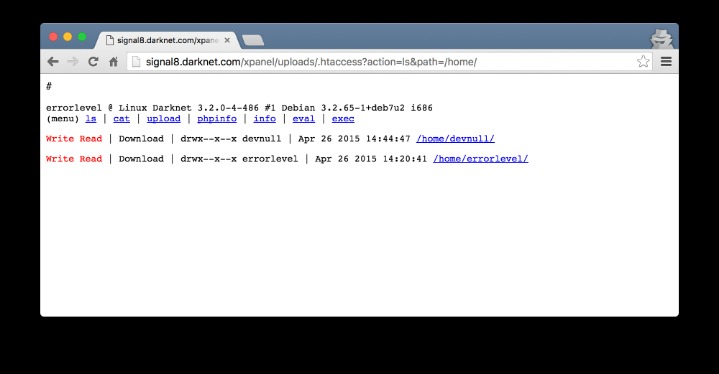
Topics And Products Sold
However, we do not advise readers to log onto this dark web mirror site; doing so would risk their privacy and that of others. We have given each crypto dark web a ranking based on our comprehensive review of the features above. As stated above, we don’t condone any activity—on the dark net or otherwise—that is forbidden by law. With the above dangers, it’s imperative to tread carefully as you step into the dark web. In addition, it has an automatic kill switch (Network Lock) that stops traffic if the VPN connection fails. Accidental leaks at the Tor entry nodes can potentially expose your IP address.
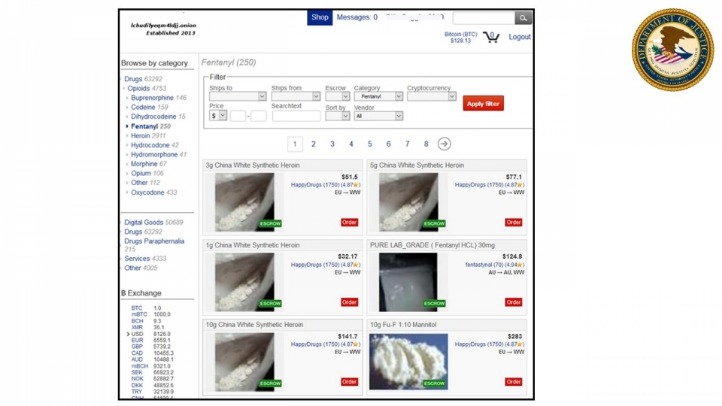
Email Services

Needless to say, it takes your data much longer to travel this way, which means dark web links load slowly compared to indexed sites. Darknet markets trace their origins to the early 2000s, with the advent of Tor in 2002 by the U.S. The first notable marketplace, Silk Road, launched in 2011 by Ross Ulbricht (aka Dread Pirate Roberts), revolutionized online black markets by integrating Tor, Bitcoin, and an escrow system. Ruheni Mathenge specializes in writing long-form content dedicated to helping individuals and businesses navigate and understand the constantly evolving online security and web freedom worlds. His articles have appeared in many respected technology publications.
II Security And Anonymity On The Dark Web
Ahmia is a dark web search engine designed to index and search tor websites. This traditional search engine is also compatible with the dark web and can help you find dark web websites. Anyone can archive or retrieve data on any site they want, wherever available. I personally recommend Tor over VPN because it’s the safer option — the VPN encrypts your traffic and changes your IP address, so the Tor network can’t see them.
This prevents tracking and fingerprinting, because Tor browser isolates each website you visit, meaning that third-party trackers and ad networks can’t follow you around. Onion sites do not use regular domain names that are registered with a central authority (domain name registry). Instead, onion sites are derived from a cryptographic key and must be accessed using the Tor browser. Buying illegal substances, stolen merchandise, and counterfeit currency or goods online poses significant risks for both the buyer and the seller. Functionally, accessing DNMs and using them requires quite a few extra steps to protect the anonymity of the buyers, sellers, and server admins. To get into DNMs, you’ll likely have to figure out the basics of things like PGP encrypted messages and using the TOR browser.
It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. You should never use your personal information on the dark web anywhere else in your life. Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web. Law enforcers can use custom software to infiltrate the dark web and analyze activities. You could be monitored closely even if you are not doing anything illegal.
The Hidden Wiki — Collection Of Popular Dark Web Links
And when it comes to paying, the site sticks to Bitcoin (BTC) and Monero (XMR) to keep transactions private. The dark web is designed in such a manner that it hides the identities and locations of its visitors. This extra privacy makes it much harder for authorities to track down who runs these markets and where they are located. For these reasons, most of these stores naturally like the dark web due to its protection.
Despite the user-friendly and familiar interface of the darknet markets, it is still a place where many criminals find their victims. Generally, complete anonymity and invisibility to the search engines are the two essential features that define the darknet. Despite the common assumption, its use is not limited to buying and selling illicit products. After all, the purpose of protecting privacy initially meant avoiding censorship, political prosecution, and proclaiming the highest value of free speech.



