Ahmia has become a trusted tool for navigating the Dark Web, with thousands of users relying on...
wpadmin
So, whether you seek refuge from oppressive regimes, are searching for answers to hard or embarrassing questions,...
Since these pages would otherwise be behind paywalls, it stands to reason that this would go against...
The Justice Department’s coordinator for child exploitation prevention, Ms. Harris, said she could not explain the poor...
Other types of crimeware kits are also for sale to initiate e.g., DDoS and ATM attacks. On...
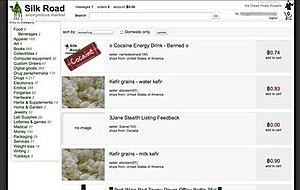
The Silk Road era was when I began tapping into online communities to share information about drug...
On the other hand, we have Tor2Web, which is a service that helps people who are not...
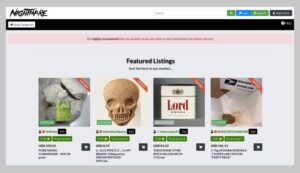
Dark web websites are pages that exist on a part of the internet that isn’t indexed by...
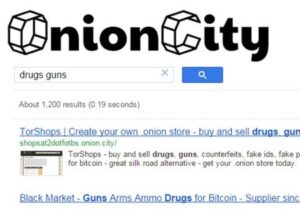
Though not a search engine in the traditional sense, OnionLinks is a categorized directory of verified .onion...
Cybercriminals often disguise malware within legitimate-looking files to trick users into compromising their own security. Once downloaded...