
That revenue went to fund the site’s operations, including servers and what the DOJ described as “employee” salaries. All transactions were conducted in cryptocurrency—primarily Bitcoin and Monero—allowing customers and vendors to move funds without using traditional financial rails. Monero’s privacy features in particular obscured sender, receiver, and transaction amounts, posing challenges to investigators tracing flows. According to TRM Labs, Incognito launched in October 2020 and remained active until March 2024. In that time, it facilitated more than USD 100 million in drug sales, including hundreds of kilograms of cocaine and methamphetamine, alongside heroin, LSD, MDMA, oxycodone, ketamine, and misbranded prescription drugs.
Seller-to-seller Network

The most important thing is to ensure that you never click on links that you’re not sure of their source. Also, it should be common knowledge not to share personal information online. The fact that there are no real regulations as well as authorities to monitor transactions, you’re always on your own, and you’re a potential target and victim of a scam or fraud. Interestingly, the hackers don’t hide, but most of them even openly advertise what they offer on the darknet forums.
Security Practices: Essential Tips
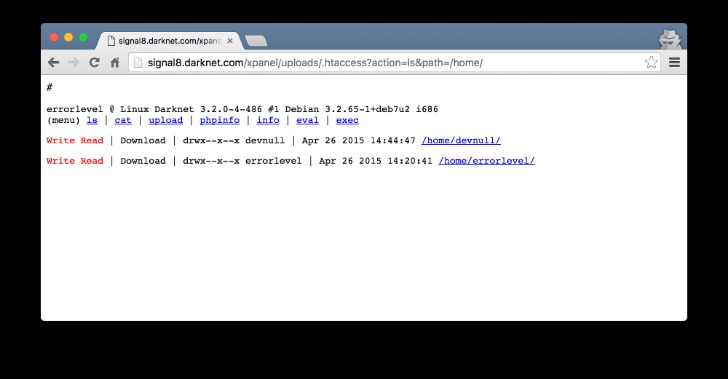
For a local machine configuration, he recommends a computer purchased for cash running Linux, using a local Tor transparent proxy. For operations security he suggests avoiding storing conversation logs, varying writing styles, avoiding mobile phone-based tracking and leaking false personal details to further obfuscate one’s identity. As the regulatory environment evolves, darknet operators and users may seek new strategies to maintain financial privacy. The rise of decentralized exchanges, privacy-enhancing Bitcoin protocols, and alternative privacy-focused cryptocurrencies could shape the next phase of darknet economy adaptations.
Network Structure Of Transactions
With the increasing adoption of digital currencies like Bitcoin and Ethereum, Tor markets will need to integrate these payment options to cater to a growing segment of tech-savvy consumers. Cryptocurrencies offer benefits such as fast transactions and low fees, making them an attractive payment method for online transactions. When one goes down, two more emerge with new ideas, better technology, and greater difficulty to track. It’s an ever-evolving ecosystem—constantly shifting, reinventing itself, and adapting.
Current markets increasingly incorporate decentralization features, privacy-focused cryptocurrencies like Monero, and specialized focuses. Some have implemented distributed hosting, robust compartmentalization, and enhanced privacy features to mitigate centralized points of failure. The darknet market landscape has evolved through several distinct generations, each adapting to increased scrutiny, technological developments, and lessons from predecessor failures. Due to law enforcement, many markets now require invites, referrals, or verified PGP identities.

Cyber-Attacks And Scams
If someone has the market’s code to the infrastructure, no matter how much effort law enforcement puts in, it will keep coming back on another server or can be built again with the same branding. What’s more concerning is that most of the time, we don’t know about these flaws, and by the time we try to fix them, we come to know it’s too late. If for any reason, you decide to visit these hidden corners of the web, ensure you at least study and understand the common traps. Getting familiar with the tactics scammers use will go a long way in helping you protect your online data and assets. Once you unknowingly install the spyware or ransomware, they can steal your identity or even hijack your crypto wallet. Too-good-to-be-true investment offers are another classic scam on the dark web.
- In contrast to the other types of sellers, the median income of U2U-only sellers increases after operation Bayonet.
- Some markets have services related to cybersecurity, while others might list more controversial items.
- Abacus Market has emerged as one of the most reputable and widely used dark-web marketplaces in 2025.
- Although derived from the marijuana plant, CBD is not psychoactive and does not contain THC.
CAMP Is Available For Trading!
A while back I made another blog post on PGP keys which helps explain what PGP is and how it works. The results further support the recent efforts of law enforcement agencies to focus on individual sellers43,44,45, as well as, more recently, also buyers46,47. Since the beginning of DWMs’ activity, there has been a shift in the law enforcement approach from focusing on market admins towards sellers and buyers9,13.
Colin and Charlie dive into the seedy underbelly of cryptocurrency—darknet markets. With $2 billion in annual volume yet surprisingly flat growth, they examine the robust review systems, exit scams, and why these sites stubbornly maintain their 2004-era aesthetics. From drug sales and breached data to scam services and malware, dark web markets are some of the most dangerous corners of the internet. These markets mimic traditional e-commerce websites, but instead of second-hand books or vintage jackets, they traffic in illegal goods and criminal services.
However, trading behaviour in DWM closely resembles what is observed on regulated online platforms despite their significant differences in operational and legal nature14. Nevertheless, due to their unregulated nature, DWMs exhibit behaviours not observed in regulated marketplaces. They offer anonymity to their users by using and developing specialized tools. DWMs are accessed through darknet browsers supporting the onion routing protocol (e.g., Tor), which provides anonymous communication connections35.
The Most Trustworthy Database For Darkweb Links
However, if we’re being honest, the majority of activity on darknet markets involves illegal or heavily regulated items. A 2020 study found that almost 57% of sites on the Tor network hosted some form of illegal content. Dark web markets have exploded in scale and reach in 2025, becoming the most dangerous hubs for trading drugs, stolen data, and hacking tools.
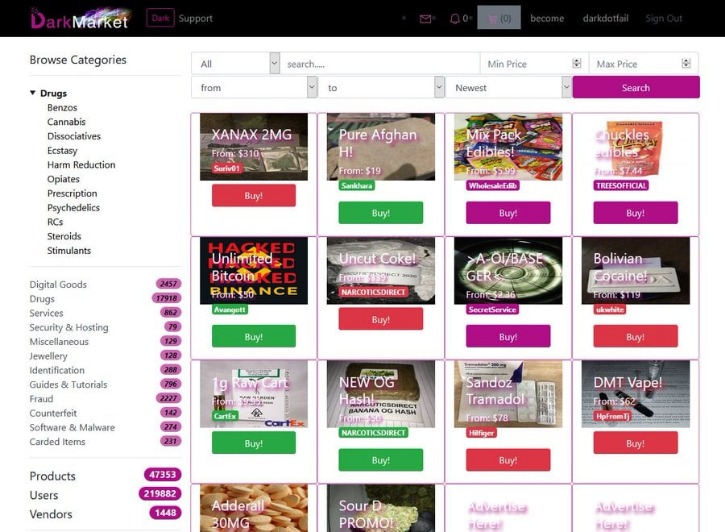
Therefore, you can hire them to perform a task for you, from planting malware to hacking email accounts and even breaking into various social media accounts. The darknet is basically an overlay network that exists within the internet and can only be accessed with specific configurations, software, and usually uses certain customized communication protocols. Always use a fake name and a temporary email address when you buy something from the dark net shops. You can even use a secure email provider or a burner email address whenever you visit the dark web. You can find featured listings on the homepage and browse the products of your choice. There’s also a search bar that you can use to search for any particular product or vendor.
External Links
The market claims to provide secure and anonymous commerce services. You can find a lot of goods and services packed with stealth high-level encryption, no JavaScript, and anti-DDoS protection. The dark web itself is not illegal, but it’s largely connected with unscrupulous and illegal operations. It is used by many for buying or selling items that are prohibited on the regular internet, like fake IDs, illegal drugs, and stolen data. Unlike regular e-commerce sites, markets on the dark web often deal with illegal or highly restricted goods and services, such as fake documents, hard drugs, and hacking services.
The dark web is only accessible through specific software like Tor (The Onion Router). Also, while this huge portion of the internet has a reputation as home to nefarious activities like hacking and drug trafficking, it also harbors legitimate activities like journalists and whistleblowers. To remain anonymous about your purchases on the dark web, always use cryptocurrency as your mode of payment.



