The website has received six Pulitzer Prizes for its grassroots-based journalism. Accessing it through an onion link is much more convenient if you’re unable to directly view it on your screen. Switzerland-based Proton (formerly ProtonMail) is one of the most secure email services, and has a reputation for not logging IP addresses.
Caution: Safety Comes First When Visiting Dark Web Links
It adds an extra encryption layer and passes your traffic through a secondary server of your choice, preventing anyone from seeing that you are accessing the web via Tor. While Tor offers anonymity on the dark web, your online activities leave breadcrumbs that can reveal your identity. That is why you should only use a reliable VPN like ExpressVPN or NordVPN for additional security and privacy.
Legitimate Reasons Why People Use The Dark Web
ProPublica is a popular online publication that won five Pulitzers in 2016. It aims to expose abuses of power and betrayal of public trust through investigative journalism. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. KEY TAKEAWAYS Whether you are using Android or iPhone, you can easily access the dark web on your ph…
Separate Your Real Life From Your Online Persona
- These links typically end in .onion instead of the more familiar .com or .org.
- Some examples include human trafficking, drug trade, weapons dealing, and pornography, to name a few.
- It enhances buyer transparency by importing vendor feedback with PGP proof.
- No, black market websites operate illegally and pose high risks of scams, fraud, and law enforcement action.
- The CIA is contactable on the dark web, providing a completely anonymous way to get in touch with them.
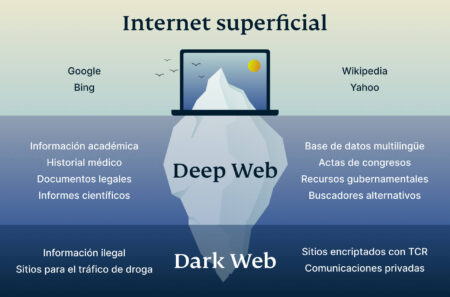
The dark web refers to a collection of websites that are not indexed by standard search engines and require specific software, such as Tor, to access. To access a dark web resource, you will need to know its web address to the letter. These websites will also use .onion top-level domain names, and many of them will be very long, random combinations of letters and numbers. You won’t be able to access .onion addresses using a standard search engine as they aren’t indexed by crawlers.
Download The Tor Browser
Phishing clones are fake copies of legitimate dark web sites or marketplaces, created to harvest login details and personal information from unsuspecting users. For developers and site operators, hosting on the dark web requires privacy, uptime, and resistance to attacks. Daniel’s Hosting specializes in anonymous hosting services optimized for Tor sites, providing secure environments and DDoS mitigation.
Encryption
Your real information could be exposed at these nodes, allowing third parties to intercept your dark web activity. That’s why we recommend connecting to VPN before accessing Tor—VPN encryption protects your data, and changing your IP adds an extra layer of privacy to protect you. When you try to connect to a .onion website, Tor will route your traffic through three or more randomly chosen nodes before it reaches your destination website. Each server adds a layer of encryption, and this layered system is what lends The Onion Router its name. With the rise in fake directories and phishing pages, knowing whether a dark web link is real has become more important than ever. A single wrong click could lead to a scam, malware infection, or even a stolen crypto wallet.
It’s simply a part of the internet that isn’t indexed by regular search engines and needs special software, like Tor, to access. However, while browsing the dark web itself is lawful, taking part in illegal activities — like buying or selling illegal goods or engaging in criminal behavior — is not. To stay on the right side of the law, be cautious about what you access and ensure you follow the rules in your region. Ahmia primarily indexes .onion sites on the dark web, not both surface and dark web content.
Husain is also a part of the vpnMentor Cybersecurity News bulletin and loves covering the latest events in cyberspace and data privacy. Established in 2022, Torzon market is one of the biggest and most diverse marketplaces on the dark web. It is considered very secure thanks to strict user validations and transparent payment and vendor review procedures. It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals. That’s why they’re often a popular means of communication among activists, whistleblowers, political organizers, and ethical hackers.
The New York Times
For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography.
Tor Metrics
Their Tor Hosting plans include all the essentials (aaPanel dashboard, MySQL database, SSD storage, DDoS protection) plus a random .onion domain. It was quite popular for selling a wide range of products and services. It offers impressive features, including PGP-signed addresses, payment via Monera, sticky and featured listings, and auto shops. In 2017, the website went offline following a law enforcement action taken by the American, Canadian, and Thai authorities, but since August 2021, it’s been operational again.

Users should be aware that engaging in illegal activities on the dark web can have serious consequences, including legal repercussions. The popularity of SecureDrop as a resource for whistleblowers has actually led to leading publications hosting their own SecureDrop URL. This allows whistleblowers to pass their information directly to those important news outlets.
Is It Legal To Access The Dark Web?
- For real-time messaging, Ricochet Refresh offers decentralized, peer-to-peer encrypted chats over Tor without central servers, greatly reducing surveillance risks.
- The use of the dark web usually means that you are attempting to engage in activity that you could not otherwise carry out in the public eye.
- Dashlane is a reputable password manager that offers useful services at very low prices.
- By acknowledging that services, communities, and security measures are in constant flux, you can better position yourself to respond effectively.
- Therefore, caution and discretion areAlways use a VPN to add an extra layer or protection.
Unlike traditional search engines like Google or DuckDuckGo, Torch indexes hidden websites that operate beyond the reach of the surface web. But users should always be cautious and avoid clicking unfamiliar or untrusted links to steer clear of scams or malware. Using a reliable VPN like ExpressVPN with dark web search engines is essential for protecting your privacy.

Although there is some crossover, the list of sites on OnionLinks is broadly different from those on The Hidden Wiki. Given the regularity with which .onions sites go offline and disappear, the more directory sites you know about, the better. Cryptocurrencies weren’t so popular among the general public until recently. However, dark web users have relied on Bitcoin transactions for over a decade, as they allow people to make payments while staying completely anonymous.
It’s a cornerstone of transparency and investigative reporting on the dark web. ProPublica made history by becoming one of the first major investigative journalism outlets to launch a .onion mirror. This version of their site allows readers in restrictive countries to access groundbreaking journalism without censorship or surveillance.