People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web. It is easily accessible by the general public and requires no special configuration. You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal.
A Collaborative Initiatives Between Law Enforcement And Financial Institutions
In Europe, for example, the Markets in Financial Instruments Directive (MiFID) II requires dark pools to provide more information about their operations and ensure that they are not harming price formation in public exchanges. Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading. Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet. It has built a reputation for being a reliable source of stolen credit card data and PII.
Discover Content
To protect against the threats posed by the dark web, businesses must adopt a proactive and multi-layered cybersecurity strategy. These measures are essential for safeguarding sensitive data, maintaining regulatory compliance, and mitigating risks effectively. Another reward of insider trading on the dark web is the networking opportunities it provides. By taking part in insider trading, investors can make connections with other investors who are also taking part.
- Always compare any URLs you access against our list to avoid scams.
- The stolen credentials allowed attackers to infiltrate the company’s email system, impersonate senior staff, and send fraudulent invoices to clients.
- These tippers then charge a fee for the information, usually in the form of Bitcoin or another cryptocurrency.
- First, we propose an algorithm that categorizes users either as buyers or sellers, and show that a large fraction of the trading volume is concentrated in a small group of elite market participants.
- Before implementing any strategies, you need to seek proper financial, legal and accounting counsel.
- The intricate methods and techniques employed underscore the sophistication of these illicit operations.
German Police Shutter 47 Criminal Crypto Exchanges
The anonymity and decentralized nature of the dark web make it an ideal platform for these types of transactions, as it allows users to remain anonymous and buy or sell stocks without fear of being tracked or identified. If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web. You can also run a dark web scan to see if your information has been leaked on the dark web.
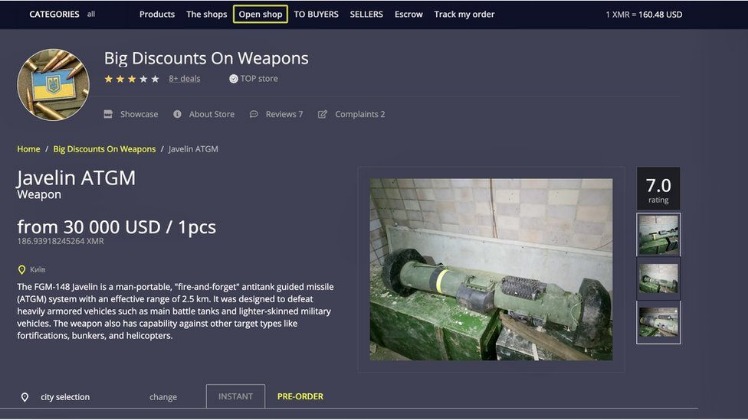
The anonymity and untraceability of the dark web allows any user to be anonymous in real time when accessing the dark web without revealing their identity to the server, including criminals who engage in illegal activities. It was quite popular for selling a wide range of products and services. It offers impressive features, including PGP-signed addresses, payment via Monera, sticky and featured listings, and auto shops.
Ready To Explore Web Data At Scale?
But this estimate varies depending on the level of trading activity across shares. But this work also shows that the relationship between market quality characteristics and dark trading varies (as predicted by Zhu, 2014 and reported for an Australian sample by Comerton-Forde and Putni?š, 2015). In the first arc of the anime series Lupin the 3rd Part V, Lupin III steals digital currency from the “Marco Polo” darknet market.

What Makes Abacus Market Stand Out In 2025
It is important for regulators, investors, and traders to work together to combat insider trading on the dark web and ensure that the stock market remains a fair and transparent place for all. Insider trading on the dark web has become an increasingly popular practice among criminals looking to make a quick profit. The dark web provides an anonymous and unregulated platform for traders to share and sell confidential information, which can then be used to make trades on the stock market. Each marketplace is a star-graph where the central node is the marketplace, and the leaf nodes, i.e., the first-neighbors, are the marketplace users. Therefore, all transactions involving the market have the market either as a source or as a destination node.
Classification Of Sellers And Buyers
As we have seen, it can be used to facilitate insider trading by providing a secure and anonymous platform for criminals to operate. Depending on the severity of the violation, investors may face criminal charges, hefty fines, and even jail time. In addition to facing potential legal issues, those who engage in illegal insider trading also risk damaging their reputation and negatively impacting their career prospects. No, black market websites operate illegally and pose high risks of scams, fraud, and law enforcement action.
This unique infrastructure fosters an environment for illegal commerce, posing significant cybersecurity risks for businesses. Here, we set out to find the main actors in the DWM ecosystem and assess their systemic impact on a dataset of 40 million Bitcoin transactions involving the 31 major markets in the period 2011–2021. First, we propose a simple algorithm to identify buyers and sellers. Importantly, the algorithm returns reasonable estimates for the number of sellers when compared against a benchmark of nine DWMs where estimates exist. Then, we reveal a concentration of activity around an elite group of participants, where a large fraction of the trading volume is driven by a small number of players.

The dark web poses significant risks to small and medium-sized enterprises (SMEs), which are often ill-equipped to handle the sophisticated threats emerging from these hidden networks. Compromised credentials, stolen intellectual property, and leaked sensitive data regularly surface on dark web marketplaces, exposing SMEs to severe financial and operational consequences. Despite its illegality, many people still turn to the dark web to engage in insider trading.
While it is illegal for insiders to share non-public information, it is not illegal for investors to speak with insiders about the publicly available information. Investors can seek out opportunities to speak with executives, employees, and other insiders to gain insights into a company’s operations, strategies, and prospects. The best way to protect yourself from legal troubles related to insider trading on the dark web is to avoid engaging in it altogether. Trading on non-public information is illegal, and the potential consequences can be severe.
The second category consists of data stores, which specialize in stolen information. In 2023, the dark web attracted an average of 2.7 million daily users, with Germany now leading as the country with the highest number of Tor users, surpassing the United States for the first time in years. Journalists use the dark web to communicate with sources anonymously, and whistleblowers rely on it to share sensitive information without fear of retaliation. Such uses prove how the dark web can serve important social functions.



