
It provides all pertinent destination information and is used to access an organisation’s web-based service. The top level domain (TLD) is the part of a URL which follows the dot, e.g. ‘com, net’. A computer network is a group of interconnected nodes or computing devices that exchange data and resources with each other. A network connection between these devices can be established using cable or wireless media. A network of infected devices, connected to the Internet, used to commit coordinated cyber attacks without their owner’s knowledge. Bitcoin is a digital currency which operates free of any central control or the oversight of banks or governments.
Use Active Monitoring Of Financial And Identity Theft
- Understanding the dark web is crucial to cybersecurity, as it can be a breeding ground for various cyber threats, including the sale of stolen data, malware distribution, and the coordination of elaborate cyber-attacks.
- These marketplaces are often ‘hidden’ online, and facilitated by individuals coordinating the trading of these goods.
- You can choose the best darknet (.onion) website that suits you and start surfing.
- And when you consider how many pages just one Gmail account will create, you understand the sheer size of the Deep Web.
- This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously.
The advantages of I2P are based on a much faster and more reliable network. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains. All of the above is why I strongly recommend using the dark web not for access to iffy or outright illegal trading of goods and services, but instead to gain access to information you might normally be blocked from. But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web. As mentioned before, your ISP and government institutions are not able to see what sites you visit on the Tor network, but they can probably see that you use Tor. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI.

Protect Yourself With Identity Plus
And my vow to you is that this government will continue to tighten the net on the cowardly keyboard warriors and those who wage state-sponsored cyber warfare. Cyber capabilities have multiplied beyond the wildest dreams of her creator. Because whilst criminals plot and hide behind their screens, their actions have real-life consequences for their victims. Here in Manchester, a gang of five university students were recently sentenced for selling more than £800,000 worth of drugs on the Dark Web to customers in Australia, Europe, New Zealand and the United States.
Shuttered Dark Web Marketplaces
This adds extra protection since opening Tor itself encrypts your traffic. NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites. It offers top-of-the-line security and fast speeds for a smooth browsing experience on the dark web. Most likely, the native account on your device has full admin permissions by default. Many malware take advantage of this vulnerability to launch an attack.
The VPN connection will route your online activity through a different server, masking your activity from your internet service provider. If you don’t have or use a VPN already, we have roundups of the best VPNs overall and the best free VPNs if you’re on a budget. Sign up for your free account today and start protecting your external attack surface from potential threats. Journalists and whistleblowers also benefit from the dark web’s privacy features. By communicating and sharing sensitive information through encrypted channels, these individuals can protect their identities and ensure their safety. The dark web offers a platform for secure collaboration, allowing journalists to report on important issues while safeguarding their sources.
Understanding The Deep Web, Dark Web, And Darknet (2025 Guide)

Another important step is to use a different email address specifically for dark web activities. By creating a separate email, you minimize the risk of your personal or professional accounts being compromised. First and foremost, make sure you have reliable antivirus software installed on your device.

Abacus Market
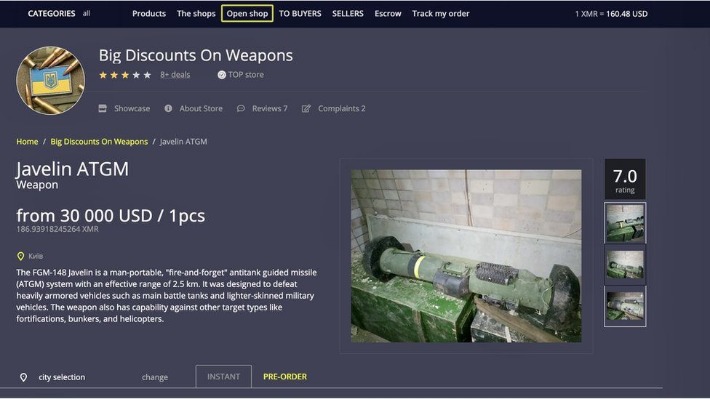
These “digital black markets” offer drugs, weapons, counterfeit money, stolen data, and more. Engaging or even just browsing can lead to serious legal consequences. While the Dark Web has garnered notoriety for illegal activities, it wasn’t created with malicious intent. Originally, the concept aimed to provide a platform for free speech, especially in countries with strict censorship laws.
What Are The Legal Risks Of Using The Dark Web?
- Many dark websites are set up by scammers, who constantly move around to avoid the wrath of their victims.
- It’s somewhere Google and Bing don’t index, and you need special tools to get to it.
- Others are looking for stolen data, hacking services, or even banned books and political content.
- Most of the password managers I’ve tested include some form of dark web monitoring or scanning in the password health section of the app.
- For example, China uses the Great Firewall to block access to Western sites.
While it offers a sanctuary for those seeking privacy, it also presents significant risks. Awareness and caution are key when navigating this hidden realm, particularly as we advance into 2024. Identity theft is yet another sinister consequence of data exposure on the dark web. Criminals can assume another person’s identity, leading to devastating consequences for the victim, including ruined credit scores and reputation. But don’t worry, you can still access Telegram in the blocked countries by simply using a VPN or a proxy. The Code for Crown Prosecutors is a public document, issued by the Director of Public Prosecutions that sets out the general principles Crown Prosecutors should follow when they make decisions on cases.
As we move into 2024, it’s crucial to separate fact from fiction and understand the realities of the Dark Web, especially in the context of the United Kingdom. If you live in countries where Telegram is blocked, you won’t be able to access Telegram. Just change your location to another country where Telegram works or use a PureVPN proxy and you’re good to go.If you want to know how to access telegram with the help of a VPN or a proxy; check out this guide. Taking on the mining tunnel metaphor, the Dark Web would be the deeper portions of the Deep Web that require highly specialized tools or equipment to access. It lies deeper underground and site owners have more reason to keep their content hidden.
Also, there’s a vast amount of unsavory content on the dark web, as well as a significantly high number of hackers and scammers looming on the platform. The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web. In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe. Keep in mind what you’re looking for, find that information, and disconnect from the dark web. As enticing as it might be, don’t follow links to other parts of the dark web.
We Went Out With The Evri Parcel Robot Dog In Leeds – Here’s What People Thought
Then, install Norton 360 Deluxe to get AI-powered scam detection to help secure your browsing against online threats. I review privacy tools like hardware security keys, password managers, private messaging apps and ad-blocking software. I also report on online scams and offer advice to families and individuals about staying safe on the internet. Before joining PCMag, I wrote about tech and video games for CNN, Fanbyte, Mashable, The New York Times, and TechRadar. I also worked at CNN International, where I did field producing and reporting on sports that are popular with worldwide audiences. Finding real dark web links is possible via some clear web forums or social platforms like Reddit, though it’s just as easy to come across phishing links containing malware or links to scam sites.
And now that it’s happening online, it’s happening to even more people. We will also be giving £3 million to continue the great work of CyberAware; our nationwide campaign to educate the public and businesses with the latest advice on how to take simple steps to protect against cybercrime. In addition there will be more money to support victims of cybercrime, improving the information they have on how their crime is progressing and being dealt with. This includes money for the National Crime Agency to support their work going after sophisticated cybercriminals and the prevention of cybercrime in the first place. Chairing the first ever cyber COBR after the incident really brought home to me how damaging attacks like these can be and how important cybersecurity is. It was sobering to learn that the National Audit Office’s conclusion was that the NHS could have avoided the crippling effects of the “relatively unsophisticated” Wannacry ransomware outbreak with “basic IT security”.
This means your activities cannot be traced or your browser history exposed. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged. Onion links have no regular domain names registered under the domain name registry. Instead, they are designed using a cryptographic key and can be accessed only through software like the Tor browser.
As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web. Keybase is a fantastic onion website that lets you cryptographically bring your different online identities together. Look no further if you want good music while navigating the dark web. ProPublica covers all the controversial stories from corrupt politicians, child labor, etc., in English and Spanish. This means you can visit the site anonymously using the Onion browser, especially if you live under an oppressive regime.



