Multi-cryptocurrency support via Bitcoin and Monero works alongside streamlined interface design and dedicated customer assistance. The vortex shop delivers extensive educational resources and vortex tor access guidance for newcomers. Integrated protection features within the vortex website system actively prevent unauthorized access attempts. Proper vortex darknet shop configuration ensures maximum privacy protection and comprehensive user security.
The kerberos mirror network forms the backbone of marketplace continuity and availability. These kerberos marketplace backup systems eliminate service interruptions during maintenance or technical upgrades following the kerberos market working urls standards. Each backup connection implements identical security measures as outlined in the kerberos trusted darknet site protocols. The kerberos onion marketplace architecture efficiently manages substantial user volumes while maintaining peak operational standards. Beginning in September 2021, Abacus Market has established itself as one of the leading dark web marketplaces. After AlphaBay closed, Abacus Market took its place as the world’s largest underground darknet marketplaces.

Since then, he has dedicated his career to writing extensively about crucial infosec, data privacy, and cybersecurity topics. When he’s not empowering PrivacySavvy’s readers to take control of their online security, Saheed enjoys distance running, playing chess, and exploring the latest open-source software advancements. Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit. Some marketplace operators first build trust by running a legitimate platform.

The site allows users to find and buy a vast variety of products and services. It’s known for its strong security features (like a trusted escrow system, PGP two-factor authentication) and anonymity. The marketplace supports multiple payment methods, including Bitcoin (BTC), Litecoin (LTC), and Cryptocheck.
Set Up Tor Browser
The website allows a personalized searching experience, where you can search according to your geographical location, country-specific, and keyword or price-specific search results. When you purchase using links on our website, we may earn an affiliate commission at no extra cost to you. Look for ratings below 90% or no escrow—common red flags on markets like Torrez.
- While it might be tempting, remember that downloading such content has serious legal and cybersecurity risks.
- In 2025, darknet marketplaces primarily accept Monero (XMR) and Bitcoin (BTC).
- We The North market onion connections preserve complete anonymity throughout all user interactions.
- Look for ratings below 90% or no escrow—common red flags on markets like Torrez.
- We The North market has emerged as a transformative force in secure anonymous commerce, revolutionizing darknet marketplace operations through its community-focused approach.
Kerberos Market – Premium Darknet Marketplace With Advanced Security

What makes this market popular is the fact that it’s less expensive compared to the rest. Nemesis Market is a relatively new wallet-less shop on dark web where you don’t need to deposit any amount in your wallet before buying products from here. The platform allows buyers to review the vendor’s products and services, so it’s easy for them to decide if the vendor is reputable or just scamming them.
Darknet Markets Generate Millions In Revenue Selling Stolen Personal Data
Abacus becoming the largest Bitcoin-enabled Western DNM may have inadvertently led to its closure. Marketplaces that reach the top of the ecosystem, in terms of volume, user base, listings, and reputation, often become priority targets for law enforcement. Archetyp’s recent takedown followed this pattern and likely influenced Abacus’s trajectory. In late June 2025, users began reporting withdrawal issues with Abacus Market, which typically indicates an impending exit scam. Darknet markets still play a role in the cybercrime economy, but their future remains uncertain.
Best Free VPNs For The Dark Web In 2025: Secure & Fast
The users on this site can review and rate the products that promote reliable and fraudster vendors. To prevent the users from DDoS attacks, it provides personal marketplace domains to high-volume buyers and sellers. Moreover, this shop provides detailed statistics about each user profile on the platform, giving users a better idea about the vendors for the buyers and vice versa. This marketplace accepts payments via Monero but also supports the Escrow system. Therefore, you must know how to access dark web marketplaces safely (covered later in this article).

Recent Shutdowns And Exit Scams
Step into a world of endless creativity, where torzon darknet dreams come to life and innovation knows no bounds. Join our vibrant community and embark on an unforgettable torzon market journey. Comprehensive validation processes govern each vortex market link before deployment. The vortex onion link addresses undergo rigorous security verification prior to public availability. Vortex market onion connections preserve complete anonymity throughout extended user sessions.
What Should I Do If My Credit Card Information Has Been Compromised?
Next, we extracted information about stolen data products from the markets on a weekly basis for eight months, from September 1, 2020, through April 30, 2021. We then used this information to determine the number of vendors selling stolen data products, the number of stolen data products advertised, the number of products sold, and the amount of revenue generated. Torzon Market boasts a large and active vendor community, offering a wide range of products and services across various categories, including drugs, fraud, and digital goods. All vendors are vetted and adhere to strict rules, ensuring the quality and authenticity of their wares. The dark web is a part of the internet that isn’t indexed by search engines.
ASAP Darknet Market
I’ve been a torzon url enthusiast for years, and torzon market has been my go-to platform for inspiration, guidance, and support. From the vibrant community to the wealth of resources, torzon market never fails to impress. Torzon mirror regularly hosts events, workshops, and meetups for torzon mirror enthusiasts of all levels.
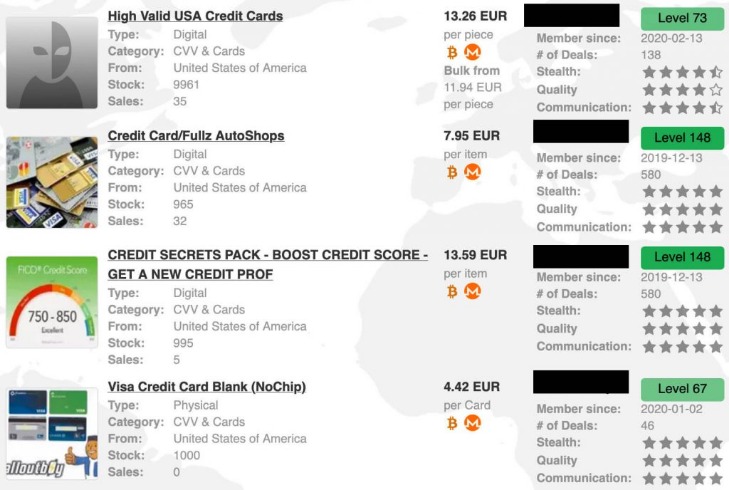
However, the effectiveness of these efforts has been a topic of debate among experts. The demand for stolen credit card information on darknet markets is high, and the supply is constantly evolving. Vendors are constantly finding new ways to steal credit card information, and buyers are always looking for the latest tools and information to make fraudulent purchases. Darknet markets also provide a platform for the development and sale of credit card fraud tools. The darknet CC market has gained notoriety as a hub for illegal activities, particularly the trade of stolen credit card information.
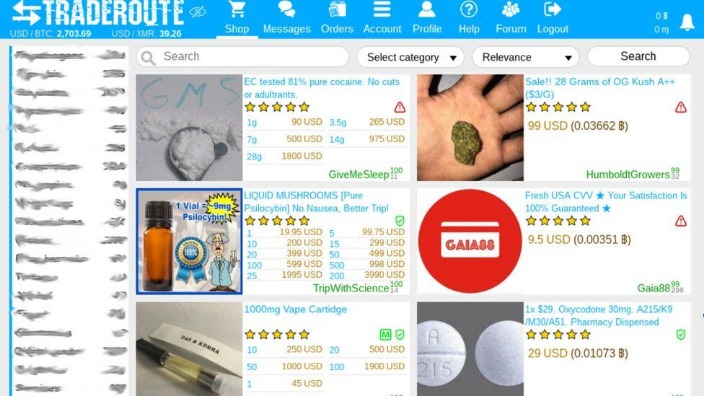
The demand for pharmaceuticals on darknet markets remains high, with a focus on prescription medications, nootropics, and performance-enhancing drugs. These products are often sourced from international suppliers, ensuring competitive pricing and a wide variety of options. Digital products, such as e-books, software, and online courses, also play a significant role in the ecosystem, catering to a diverse audience. In conclusion, the darknet continues to evolve, providing a secure and efficient platform for drug trade. By 2025, markets like PhantomX, NebulaTrade, and EclipseMarket are expected to dominate, offering users a combination of privacy, reliability, and variety.
Whether you’re new to the dark web or a vet who’s seen it all, you’ll find something here to chew on. Below, I’m breaking down each market with everything I’ve picked up—listings, quirks, the works. Things like IP addresses, ports, and volume of traffic, but not the full packet capture. Upon putting a pen trap on the server they found hundreds of computers around the world are connecting to the server and uploading credit card data to it. Detective Dunn started visiting any of these places that were local to Washington State where he was based out of. Similar point of sale software, similar malware, logs showed Remote Desktop connection, and then the malware was downloaded.