I wanna provide labelled products, good advice and service, like a real business. Not sit in a shitty car park selling $10 bags from a car window all day. The most recent example is the shutdown of the oldest marketplace Hydra Market in 2022 which took a combined effort of the FBI and the German authorities. Unfortunately, that as well didn’t stop other darknet markets from rising. The darknet markets keep on popping even when the authorities keep getting hard on them.

Leverage Free Cybersecurity Resources
- Even after Silk Road went down, dark web marketplaces haven’t slowed down.
- This vetting process helps keep the community “clean” from spies, law enforcement, or anyone who might pose a risk.
- Security professionals, however, remain vigilant, well aware of the risks and dangers that lurk behind the veil of anonymity.
- It also requires users to verify their identity carefully to build trust with buyers focused on fraud.
- The first thing on the minds of many users when it comes to the dark web environment is illegal drugs.
The dark web is famous when it comes to hosting as well as spreading explicit and illegal content. It is home to all sorts of disturbing content, given that the markets share content related to non-consensual recordings and child exploitation. Perhaps, hiring a hacker can feel impossible, but it’s a genuine threat that you need to be aware of. In fact, several businesses can use that service to get rid of competitors, or individuals can use it to gain access to personal information about someone. Interestingly, the hackers don’t hide, but most of them even openly advertise what they offer on the darknet forums. Therefore, you can hire them to perform a task for you, from planting malware to hacking email accounts and even breaking into various social media accounts.
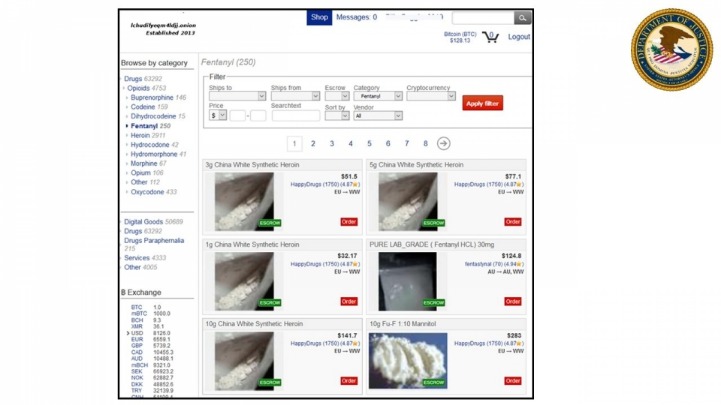
Usually dark web transactions are made with Bitcoin or other cryptocurrencies. Dark web marketplaces are structured platforms that mirror legitimate e-commerce websites but thrive on anonymity and untraceable transactions, often conducted through cryptocurrencies. According to a report by Kaspersky, a single stolen credit card can be purchased for as little as $15, while entire company databases are sold for significantly higher sums.

Conduct Cybersecurity Risk Assessments

Buyers browse listings, place orders, and pay with cryptocurrency — typically Bitcoin or Monero — to obscure transaction trails. One of the biggest mistakes someone could make while buying off the dark web is using a credit or debit card. Their bank, along with law enforcement, would have complete insight into their purchase. Instead, it’s best to open a crypto wallet and buy some cryptocurrency, like Bitcoin or Litecoin. Saheed Aremu passionately advocates for digital privacy and cybersecurity in the modern digital age. As one of PrivacySavvy’s resident VPN experts, he guides readers on protecting their online information and anonymity.
This malware-as-a-service model allows less tech-savvy criminals to launch malware-driven cyberattacks without building the tools themselves. Law enforcement agencies monitor many dangerous markets, and even anonymous browsing isn’t foolproof. Just visiting these sites can attract attention from law enforcement, especially if you interact with known vendors or download suspicious content. In this article, we’ll explore what dark web markets are, how they work, and why they’re so risky.
Primary Risks For Users Of Darknet Marketplaces
It has built a reputation for being a reliable source of stolen credit card data and PII. Renowned for its extensive inventory of financial data and sophisticated operating methods, Brian’s Club is a key player in the underground economy of financial cybercrime. This structured process ensures security while maintaining the anonymity of both buyers and sellers, making Dark Web marketplaces a persistent challenge for cybersecurity enforcement.
How To Secure Your Bitcoin Wallet?
Furthermore, regular cybersecurity risk assessments would have identified weak authentication systems, allowing the firm to implement stronger measures, such as multi-factor authentication. In 2021, a small marketing firm experienced a devastating data breach after employee login credentials were compromised and sold on a dark web marketplace. The stolen credentials allowed attackers to infiltrate the company’s email system, impersonate senior staff, and send fraudulent invoices to clients. Within days, the attackers had exfiltrated sensitive client information, including proprietary marketing plans and billing data.
When Is The Right Time For A Business To Buy Trustpilot Reviews?
Some get hacked, some get shut down by law enforcement, and some succumb to their own greed – whereby the operators ‘exit scam’ entire communities. This is why there’s no specific endorsement for any particular marketplace I can make, but I’ll include a few of the most common below for reference. By carefully evaluating sellers and products, you can enhance your chances of having a positive buying experience on the Dark Web. However, remember that there are risks involved, and engaging in any illegal activities or purchasing illicit goods is both unethical and illegal. It is crucial to recognize that not everything on the Dark Web is illegal or malicious.
Seller’s Reputation And Capacity On The Illicit Drug Markets: 11-month Study On The Finnish Version Of The Silk Road
Thus, regardless of which of the pair you intend to use, you should start by buying bitcoin. A quick and relatively private way of doing so is to use a peer-to-peer market such as Localcryptos.com. This enables you to buy bitcoin from private individuals, who will accept payment into their bank account, as well as alternative methods such as Paypal, Alipay, and Moneygram. A full explanation of how to make a bitcoin purchase on Localcryptos follows below. The Dark Web is used by cybercriminals to buy and sell illegal goods and services, coordinate attacks, distribute malware and phishing kits, and share other prebuilt exploits. But, perhaps a big surprise to anyone thinking the Dark Web is just for criminal activity, it can also be leveraged for legitimate purposes.
Finding the correctly represented URL for a particular domain in the first instance can be a challenge. There are hundreds of marketplaces to choose from, each with their own set of communities, politics, and socio-economic motivations. I wont list them all here, as unfortunately not all survive long enough to outgrow the impulse of real-world influence and fallible human desires.


Amidst the shadowy corners of the dark web, Royal Market stands tall as one of the most enigmatic and concerning marketplaces. Security professionals are keeping a close eye on this elusive platform, known for its vast array of illegal goods and services. Its rise to notoriety has put it among the top 5 dark web marketplaces that experts worry about. With stringent security measures and a thriving community, Royal Market poses a significant challenge in the ongoing battle against cybercrime. The magnitude of illegal trade on these marketplaces is astounding, with transactions reaching millions of dollars. The lucrative nature of dark web activities fuels the growth of more such marketplaces, perpetuating the cycle of criminal behavior.
- He’s so worried that people will discover his double life that he risks overdosing alone.
- This extra privacy makes it much harder for authorities to track down who runs these markets and where they are located.
- Governments and police have made real progress in shutting down big darknet markets.
- Here i have described how to install tor in step by step process with images and how to stay anonymous.
- This was an intriguing boast—a prosecutor told me it was made to gain users’ trust—but it was untrue.
- Hydra also featured numerous vendors selling false identification documents.
Top-10 Dark-Web Marketplaces In 2025: Overviews, Use-Cases, And Risks
Businesses face substantial cybersecurity risks due to the proliferation of these marketplaces. Data breaches often lead to sensitive corporate information appearing on the dark web, which can fuel further attacks. A security gap analysis can help businesses identify vulnerabilities that hackers exploit to compromise their data.
The platform supports Monero (XMR), Bitcoin (BTC), and several others to hide identities. Also, set up two-factor authentication (2FA) to add an extra layer of protection in case someone manages to figure out your password. Moreover, if you must use public Wi-Fi, ensure that you use a VPN to mask your browsing activity and keep yourself secure. In this era, it takes one wrong click and all your sensitive data ends up in the wrong hands. Therefore, you need to take your privacy seriously and start by using strong and unique passwords for every online account you open. Stuff that I already know is that you should not use your real name, you have to convert your money to crypto for purchases and it doesn’t hurt to use a vpn for extra security.
Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. If you have to email a message or files to a vendor, secure your communication with PGP (Pretty Good Privacy) encryption. This makes sure your messages are encrypted and only readable by the recipient. It’s also about practicing good operational security (OpSec) to help protect yourself and your money. Dark web directories, such as the “Hidden Wiki,” can direct you to authentic. But those directories may not be 100 percent reliable themselves, so take any information with a grain of salt.



