
This article lists some of the best dark web websites you can visit securely. Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun. Today’s markets reflect a decade of evolution, balancing user demand with operational security against an ever-present cat-and-mouse game with authorities.
- Purchases through links on our pages may yield affiliate revenue for us.
- It is the dark web’s version of Wikipedia with a massive links directory.
- Our research shows that, like most legal commodities, stolen data products flow through a supply chain consisting of producers, wholesalers, and consumers.
- The site gives out free samples of the stolen data every now and then to gain more customers.
Market Value And Popularity
Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. Many people go to the dark web to buy things they can’t find elsewhere, but what if what you’re buying is also trying to harm you? Scammers on darknet markets claim to offer legit tools or services, but instead provide you with malicious software that can infect your device.

You only need to upload your PGP key or let the platform create one. Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook. This .onion link makes it impossible for hackers to impersonate your profile. Also, you can set a strong password to protect your message and choose how long it will take to expire. Formerly known as Archive.is, it is one of the best onion sites on the dark web. It aims to preserve the internet’s scientific and cultural heritage.
Cyber-Attacks And Scams
In 2025, many platforms have adopted decentralized architectures, reducing single points of failure that previously made them vulnerable to law enforcement takedowns. On one hand, it offers privacy for whistleblowers, journalists, and citizens in oppressive countries. On the other hand, it’s notorious for enabling illegal activity, including drug sales, weapons trafficking, counterfeit ID trading, hacking services, and the exchange of stolen personal data. In fact, everything is in English, and the site picks up users everywhere in the world.
Search Code, Repositories, Users, Issues, Pull Requests

Dark web markets are hidden online platforms in Tor where users anonymously buy and sell goods and services. Next, we extracted information about stolen data products from the markets on a weekly basis for eight months, from September 1, 2020, through April 30, 2021. DarkMatter Market is a secure darknet marketplace offering multisig escrow, verified vendors, and full PGP support. The darknet has evolved into a decentralized marketplace where buyers access a wide range of products with fewer barriers than traditional platforms. Unlike centralized systems, these markets operate on distributed networks, reducing single points of failure and enhancing reliability. Vendors offer everything from pharmaceuticals to rare substances, catering to niche demands without excessive regulation.
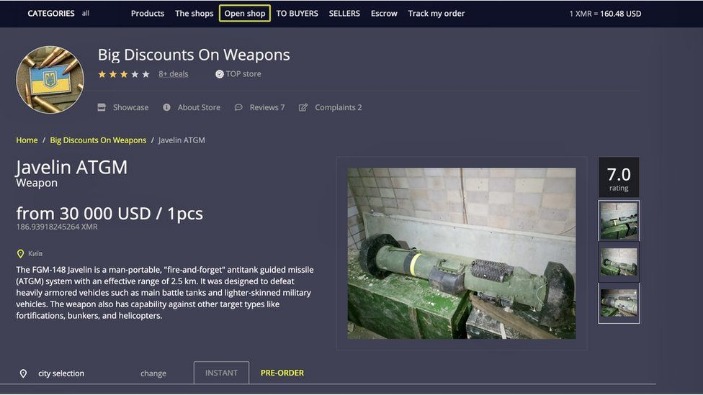
Top Markets
Another notable security trick Wasabi uses to verify transactions is the Neutrino protocol. It assigns a task to the client instead of the server, eliminating server-related vulnerability. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction. This makes it extremely difficult to find out who you are transacting with.
Tor2door Market
For these reasons, most of these stores naturally like the dark web due to its protection. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024. Some markets are invite-only or have strict registration rules to keep out scammers and law enforcement.
Dark Market Onion
It doesn’t use JavaScript, meaning the website won’t track your activities or exploit vulnerabilities. The website allows a personalized searching experience, where you can search according to your geographical location, country-specific, and keyword or price-specific search results. To turn it on, just go to the “Settings” and then the “Tools” section of the NordVPN app and activate “Dark Web Monitoring.” In the end, it’s all about staying one step ahead.
All transactions protected by multi-signature escrow to prevent scams. The dark web hosts a variety of illegal activities, many of which fuel cybercrime and real-world harm. Since 2020, 2easy has sold massive stealer logs with sensitive data like passwords, bank cards, and initial access credentials. It supports operations in multiple languages and operates on both clearnet and Tor. In the first arc of the anime series Lupin the 3rd Part V, Lupin III steals digital currency from the “Marco Polo” darknet market.
Explicit And Illegal Content
Users must first install the Tor browser, which is available for multiple operating systems including iOS, Mac, Windows, and Android. This browser allows users to reach Archetyp through its onion address, a unique URL that is only accessible within the Tor network. As the DNM builds a small pool of users and sellers, it will snowball into a lucrative operation IF the service remains reliable and secure. Besides ever increasing hosting costs, the site will have to contend with authorities, attacks from hackers, and the occasional disgruntled market administrator. Once the website is coded, the policies created, the admins ready, and the hosting secured, the site goes live on the TOR network.
Every successful referral brings lifetime commissions from completed transactions. Ethically, they must minimize harm, responsibly handle any stolen or sensitive data (often notifying victims or law enforcement), avoid entrapment, and maintain research integrity. With every action encrypted and every identity compartmentalized, users step into a framework where operational security is not a feature — it’s the foundation.
Darknet Markets Make Drug Trade Easy And Safe

In 2025, 95% of markets prefer XMR over BTC’s public ledger, with transaction volume up 60% since 2023. Stay one step ahead of dark web dangers — connect with the NordStellar team today to learn how to keep your data safer. To use social login you have to agree with the storage and handling of your data by this website. Further market diversification occurred in 2015, as did further developments around escrow and decentralization. Use Norton VPN to encrypt the data you send and receive and surf more anonymously. mark it means it has been verified as a scam service and it should be avoided. We deliver contextualized, actionable intelligence through our dedicated platform or API integration, ensuring that you can respond effectively to darknet threats. With over 20 years of experience in cybersecurity and marketing, Ben has held leadership roles at companies like Check Point, Cognyte, Cylus, and Ionix. Fill out the form to speak with our team about investigative professional services. Any drug marketed as an opiate, be it pressed pills or heroin, may also contain amounts of tranquilizers or fentanyl. While pressed pills are often made with vitamins, it’s impossible to know that the additives are safe.}
This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. The darknet in 2025 is a thriving, evolving ecosystem of anonymous marketplaces accessible via Tor. Driven by demand for privacy and illicit goods, these top 10 markets—featuring Alphabay, Archetyp, and more—offer unparalleled variety, security, and resilience despite law enforcement crackdowns. This guide provides verified .onion links, market stats, and expert insights into Tor and Monero usage as of February 21, 2025. BlackOps is a high-security darknet marketplace built for operational anonymity and precision. Drawing inspiration from covert operations, BlackOps emphasizes stealth, speed, and strict vendor accountability.
So, if a “business opportunity” sounds too perfect, it probably is. It’s also a marketplace for digital mercenaries; you’ll find everything from solo hackers offering their skills to well-organized groups that take on more complex or high-stakes projects. Some even have connections to criminal organizations and, in more serious cases, government-backed operations. Purchases through links on our pages may yield affiliate revenue for us. We review and list tools and products without bias, regardless of potential commissions. It has a bidding feature, with new batches of stolen data being frequently added.



